- cross-posted to:
- worldnews
- cross-posted to:
- worldnews
deleted by creator
The pagers that detonated were the latest model brought in by Hezbollah in recent months, three security sources said.
I wonder if Israel has a unit similar to the NSA’s TAO (tailored access operations) where they inserted people into the manufacturing plant to tamper with devices before they even left the factory.
This is more simple than that. They’re sending a malicious payload to the target numbers which causes the pager to heat up the battery and explode. Nothing manufacturing related.
I would love to see a detailed technical explanation for how this would be possible.
I design battery-powered electronics for a living and I can’t think of any design that would let a battery explode with the violence these did, let alone on command. Unless it were deliberate.
Best I can get is figuring out a way to reuse some pins on the uc to isolate two or three caps to use as voltage pumps and then dump the whole thing at once into the battery.
I somehow suspect Electroboom is going to get a lot of new viewers in the next few days
Reading a bit more into it, seems all of them were
MotorolaApollo Gold pagers (I stand corrected), so they had to have exploited the li-on charging pins to either create a loop causing thermal runaway, or spam different voltage discharging signals via their payload. Regardless, it’s a truly impressive exploit.You must have read that wrong - this was clearly committed by Israeli super spy Moty Rola.
Seriously though - they were all from a single Iranian supplier, not Motorola (at least according to every source I can find)
Yeah, news still coming in, hard to make sense of it all. I am now seeing models in the attack as being: Apollo Gold AP-700, AP-900 and AR-924.
Ap-900 Battery electrical specs: 10-30VDC or 8-18VAC Input 3-40VDC/25VAC Standby <10mA Active <100mA Tolerance -10’C ~ +50’C
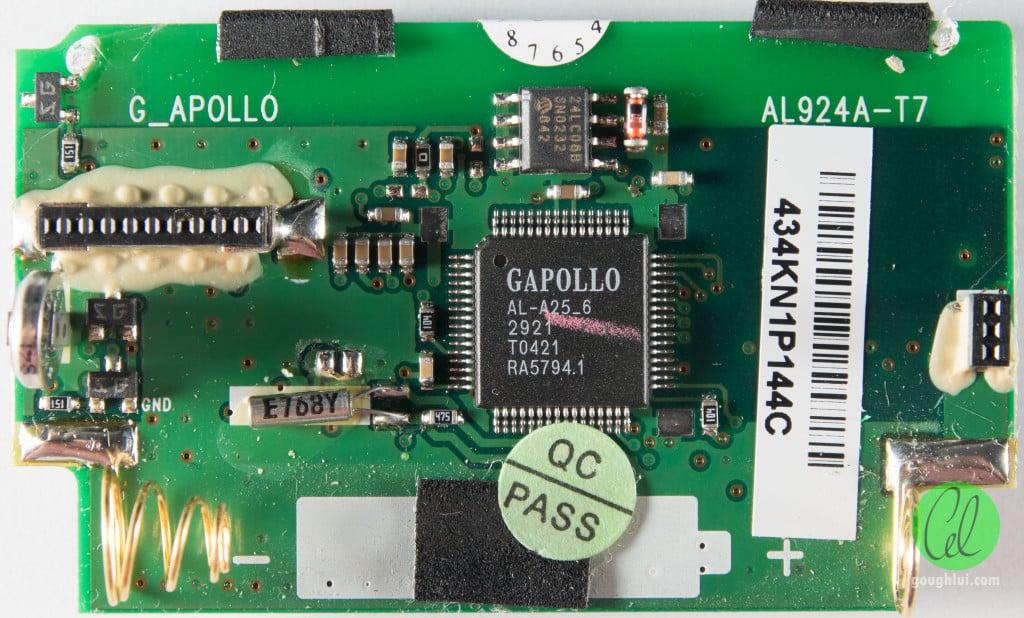
Ah. So the G_Apollo AL-A25 logic chip used in these models is programmable and unlocked by default lol.
Programmable chip responsible:
GAPOLLO AL-A25_6 RA5794.1 chip = AP-900 and AR-924 models
Do you have a datasheet link for that chip? I get results for a different pager module when I include “AL-A25_6” and zero results with only “RA5794.1”
Same here. Like, there has to be some kind of specific vulnerability in these pagers, right? You can’t just “heat up the battery,” you need something that will actually use the power. If the pagers weren’t compromised between the manufacturer and the recipients, then there’s some major fuckery afoot.
Here’s your detailed tech possible explanation with citations:
Pagers known used in the attack were Apollo Gold AP-700, AP-900 and AP-924, which all use the same ALA25 programmable logic chip.
If you google the Gold Apollo AL-A25 Programming Manual and look for battery gauge inputs, you can see it is possible to program the voltage ranges.
By setting the battery gauge level-high to an invalid selection that is also greater than the low level it creates a bridge between the anode and cathode, resulting in thermal runaway which will in fact cause the battery to overload and explode due to the increased temperatures.
We’ve done this using similar batteries on battery backed write cache controllers sitting in a nema-3 enclosure just to see what the tolerances are.
Edit Citations:
https://www.mitsubishicritical.com/resources/blog/thermal-runaway/
https://www.apollopagers.com/support/al-a25-gold-pc-programming-manual/
Programmable chip responsible:
GAPOLLO AL-A25_6 RA5794.1 chip = AP-900 and AR-924 models
Just so you know, we can tell you don’t know what any of that means.
Oh please educate me troll. I am waiting.
By setting the battery gauge level-high to an invalid selection that is also greater than the low level it creates a bridge between the anode and cathode, resulting in thermal runaway which will in fact cause the battery to overload and explode due to the increased temperatures.
First part of this is gibberish. Second part is just describing a short of the battery, which will destroy it, but is completely inconsistent with video footage which shows small high explosive charges going off. That is not how battery shorts happen. This was not done in software, there were actually explosives installed in the devices as reports are starting to now state. But you know, good job on the sheer volume of words you wrote.
Surprised you responded, I’ll respond back later when I get home so I can share the level of detail it is I am talking about.
Thank you for reminding me, edited in the citations. Back to work.
Being in IT and having worked on asics, breadboard design, lsf, dgx and others for a storage chip design company, it’s not exactly rocket science to overload a small battery so much it heats up above 140’'F/60’C that it combusts.
Here’s the initial report:
https://www.lbcgroup.tv/news/lebanon-news/796406/understanding-the-pager-and-how-it-can-explode/en
combusts
Not what happened here, and you’re still wrong.
~~This is nuts, from a vid I saw it was an actual explosion. The fact that so many “terrorists” were given devices with explosives in them and it was undetected until they blew…
I don’t care if it’s for the greater good, any entity that has the ability to pull this off should be dismantled and charged with crimes against humanity. This can’t be a thing humanity just accepts as a possibility. Yeah terrorism is bad but this is fucked if true.~~
Edit: if this video isn’t completely made up it looks like those batteries can explode. I was under the impression they would shoot flames well before any explosion, might not be the case. Quite curious on the exploit though. What conductor do they have in there that wouldn’t burn out like a fuse before the explosion.
Uhh… Terrorism where innocent citizens are targeted is worse than specific targeting of terrorists themselves.
Thank you for saying this, I was a little taken back by what in my opinion seemed to be comments expressing sympathy for Hezbollah.
deleted by creator
Here’s a video of one of them exploding.
https://youtu.be/h4McyQ8YAQI?si=GbSXpCzqH-9GKAPa
One of the deaths I read was due to ammunition in their pocket and another due to them crashing their car after it exploded. Seems 8 dead, almost 3,000 injured from Lebanon to Syria and one in Qatar.
Right, do lithium batteries exploded like that? Burst into flames sure, but explode with no apparent fire?Edit: apparently they can. I’m completely off base. https://www.youtube.com/watch?v=iDaPP-dI9dE


