“Your selected password is already being used by SwiftyFan05. Please choose another password.”
another_password
Lol I recently have found the opposite!
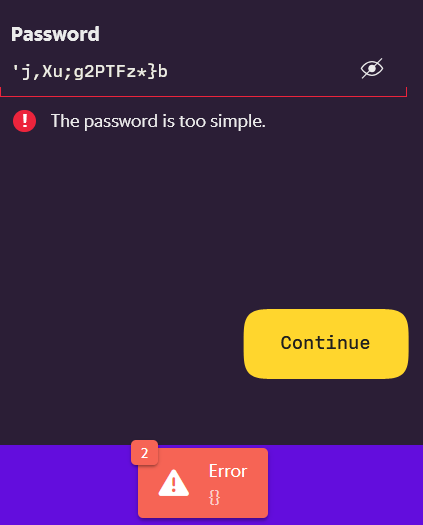
Might be a minimum of 16 chars. Or the parsing is broken and treats the ’ as the end of the password
deleted by creator
I let my password manager create 32 char passwords, that should be enough for a while. But of course then you have websites that throw you a ‘your password is too long’ message and have you find out by trial and error that they only accept 12 characters.
Or the off-by-one errors where they insist that 24 chars are the max, but in reality they accept 23. Probably never tested the limit.
Or websites that truncate your password after X characters when registering, but not when logging in, so you end up with an incorrect password and good luck finding out which limit the registration page actually uses.
That’s a big rainbow table. Like, with just precomputed values and random ascii character passwords it’s on the order of 1042 entries. You can shave that down a bit probably with all the tricks rainbow tables use, but I think you’re safe.
deleted by creator
1031 is ridiculously huge too. The NSA probably works on EB scales, which is “only” 1018 bytes. If you can get up to 1022 equally likely passwords you’re fine against dragnet, brute force-style attacks. (If you’re zombie Bin Laden and the NSA will stop for a whole year cracking your drive, and doesn’t have any shortcuts, maybe you need 1039 I guess)
That being said, if more characters is no problem, go ahead and do that. I’m not saying more security for free is a bad thing.
Fandom is gross anyway. Contributing to independent wikis is a much better use of your time. https://getindie.wiki/
It’s not Fandom
they don’t specify a limit so 64 character password it is.
Go all in, 1024 character password.
They’ll accept it, but won’t tell you they ignored everything after character n, and their login page won’t take anything but the “correct” password so you’ll be spending some time figuring out the actual character count limit…
deleted by creator
I have experienced this far too many times.
My previous bank forced 8 characters with only numbers and letters.
Hunter2
I don’t get it, why did you type all asterisks‽
What’s not to get? He made his password 7 asterisks. Funny, because it’s the same as mine.
We are all hunter2 on this blessed day.
64 characters picked at random in
[]is perfectly fine if password is your only option. Special character do not increase significantly the difficulty of bruteforcing it, but introduce the risk of having to manually type"}à.å÷Â!!ç-×ô@¸Á¢±ãÕß>>úÓ}¼º¤«<_`àÅû§Æ]*ÂñçÌÿ§à®&ܱ=Ú-´ð¹é$.>=;Öif something goes catastrophically wrong.Not being allowed to use special characters can be a sign of the website saving your password in plain text.
It can be. Or it can be someone that had to deal with users (or was trained about it) and is limiting the chances of a user being kept out because they type something that looks like their password but isn’t, and then have to go to support.
It’s actually nice they have underscore. 😀
Yes because if you choose 8 characters at random, with 25 small + 25 big letters and 10 numeric, it* only 60^8 = 167,961,600,000,000 combinations.
I think the problem is more if the system allows brute force with thousands of erroneous attempts.
Then statistically any hacker can attempt several accounts, and ultimately get lucky. But by all means, put the responsibility to the user, users are the experts right!?
I never got the frantic excessive entropy mindset, when the problem is much simpler to not allow crackers endless attempts. You can allow 50 attempts, and chances would be very slim to guess even pretty moronic passwords.What’s even worse is when they REQUIRE big and small and numbers to maximize entropy, they actually make statistically FEWER attempts necessary to brute force it.
A standard Microsoft introduced in the 90’s, and FUCKING almost everybody is using, despite it’s a 100% moronic requirement.
Instead just warn against passwords that can be guessed by logic, or can be found in a dictionary.Most websites don’t allow multiple failed logins and, even if they did, the network latency alone would make brute force attacks useless. The point of having a high entropy password is to protect against hackers brute forcing a leaked database of hashes. Having different passwords for every website also protects against this so, as usual, the answer is “just use a password manager”.
The point of having a high entropy password is to protect against hackers brute forcing a leaked database of hashes.
I don’t think you need to worry about that in this case, the special character restriction suggests to me that they don’t hash it.
just use a password manager
I will never do that, I have a system instead. I never understood why people would want to use a password manager. To me it seems it ads an attack vector, where you could lose EVERYTHING!
I guarantee your system is less secure than the worst password manager. Humans are inherently bad at choosing passwords, or anything to do with randomness really.
That is true for online password managers, you need an offline one
The point of having a high entropy password is to protect against hackers brute forcing a leaked database of hashes.
Seems a bit stupid if a database of passwords or other sensitive information can be brute forced.
Please clarify what you mean because your comment is giving me these vibes.
what’s an example of password that can be guessed by logic?
Something that can possibly be deduced knowing personal information, like a birth date.
hunter2
recently did one that only cared about being very long, so i typed thispasswordisfuckinglong and it took it
Password length is more secure than complexity.
At least if you ever forget it, they’ll be able to email it to you.
Try this one, has lots of special characters:
a_a_a_a_a_a_a_aThis one too: _____________
or the entirety of the Bible with special characters removed and spaces replaced with underscores
I hate these arbitrary limitations of 16 characters, 25 is unbreakable and some sites won’t allow longer than 16 20, I’ve even had one site not allow over 6.
Use a password manager
I mean, 63^6 is a lot of possibilities, but just make the password longer to increase its security.
Blocking out special characters is dumb, but as others have pointed out, they’re probably not sanitizing inputs.
Ah, I’ve done that before, 1/100 odds it’s because someone doesn’t want to fuck with RegEx.
You might want to try out: https://libraryofbabel.info/random.cgi
It says NO special characters!











